I decided to go with a machine that had a focus on using Wireshark, and h4cked was at the top of the easy list. Since I consider myself somewhat of a newbie when it comes to analyzing packets, I figured an easy machine would be the way to go. Let’s get started.
They start by giving us a pcap file to analyze. After firing up Wireshark and loading the file, I decide to follow the TCP stream on the first packet just to see what might be going on.
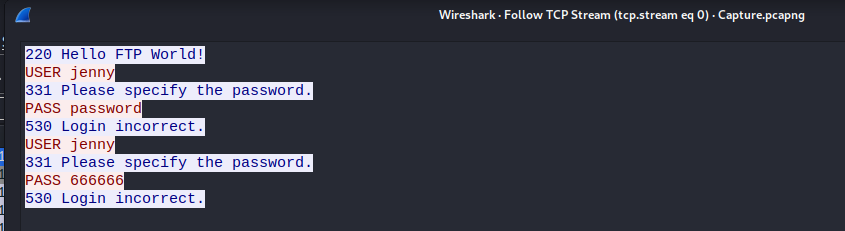
From this information we can see the attacker is attempting to login to the FTP server using jenny as the username. It also looks like they are trying some common passwords, possibly a dictionary attack. This gives us the answers to the first couple of questions on the challenge:
The attacker is trying to log into a specific service. What service is this?
FTP
There is a very popular tool by Van Hauser which can be used to brute force a series of services. What is the name of this tool?
A quick Google search of 'van hauser brute force' brings up the github page for the hydra tool as the first result. Hydra is the answer.
The attacker is trying to log on with a specific username. What is the username?
jenny
The next question asks us what the password was. We know from looking at the first TCP stream they did not guess the correct answer, so lets scroll through the other TCP streams in the pcap file and see if anything shows up. Once you are in the TCP stream box, you can scroll through the different streams by clicking on the up or down arrows in the bottom right of the pop-up box. When we hit stream seven, we see a ‘Login successful’, giving us the password!
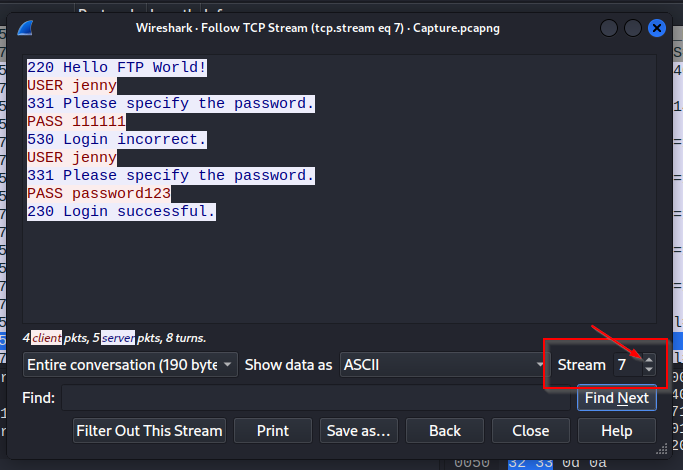
What is the user’s password?
password123
We keep scrolling through the different streams, following the attackers moves. When we hit stream 16, we see some action.
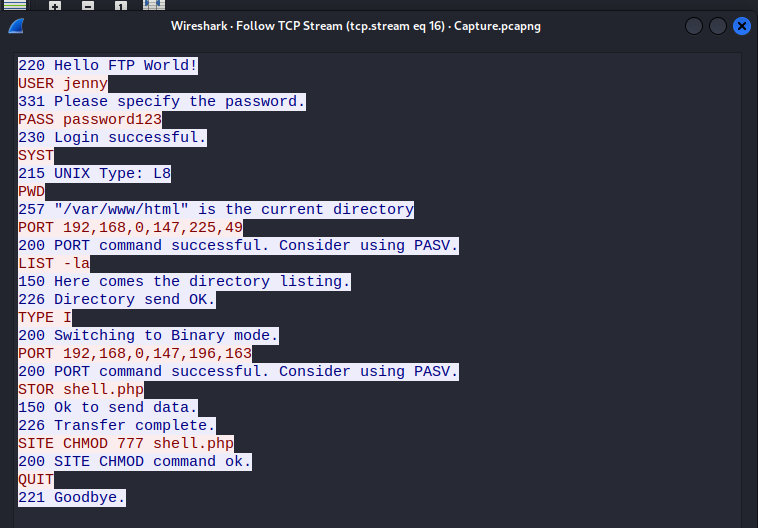
This shows us the attacker logging in and issuing a variety of commands. They first confirm the directory they are in with the PWD command. Then they upload a file called shell.php and give that file permissions to run on the victim’s machine. As of right now we don’t know what’s in that file, but there’s a pretty good chance its a reverse shell. When reverse shells are run, they will call back to the attackers machine, providing the attacker a shell on the victims machine. This will allow them to run commands, and potentially escalate privileges to get administrator rights on the victims machine.
This gives us the answers to the next couple of questions:
What is the current FTP working directory after the attacker logged in?
/var/www/html
The attacker uploaded a backdoor. What is the backdoor’s filename?
shell.php
Continuing through the streams we come across the file that was uploaded, shell.php, and all of its code. This confirms my previous suspicion of the file being a reverse shell. Looking through the code, its actually a quite popular reverse shell from pentestmonkey.net. In fact, this is a reverse shell I use myself quite a bit, so its easy to identify where the reverse shell is pointed to, 192.168.0.147 port 80. It also contains the answer to the next question:
The backdoor can be downloaded from a specific URL, as it is located inside the uploaded file. What is the full URL?
http://pentestmonkey.net/tools/php-reverse-shell
We get to the last stream in the pcap file and get to see the commands the attacker used through their reverse shell. They start with some common commands to get a lay of the land, determining who they are logged in as with the ‘whoami’ command, and then listing the files and directories to see what they have access to. Then they use python to create a more interactive shell, and then su into the jenny account using the password they found from earlier.
Once in the jenny account, the attacker runs the ‘sudo -l’ command and finds out they can run any command with sudo privileges without a password.

Having the ability to sudo any command without a password means root access to the machine. The attacker uses this security misconfiguration and runs sudo su to log in to the root account. Before going any further, let’s go ahead and answer the next few questions:
Which command did the attacker manually execute after getting a reverse shell?
whoami
What is the computer’s hostname?
wir3
Which command did the attacker execute to spawn a new TTY shell?
python3 -c 'import pty; pty.spawn("/bin/bash")'
Which command was executed to gain a root shell?
sudo su
The next set of commands shows the attacker cloning the Reptile rootkit to the victims machine. Rootkits are typically used to establish persistence on a machine so the attacker can access the victims machine much easier later on. Looking at the github page, the features of the Reptile rootkit include many things beyond persistence:
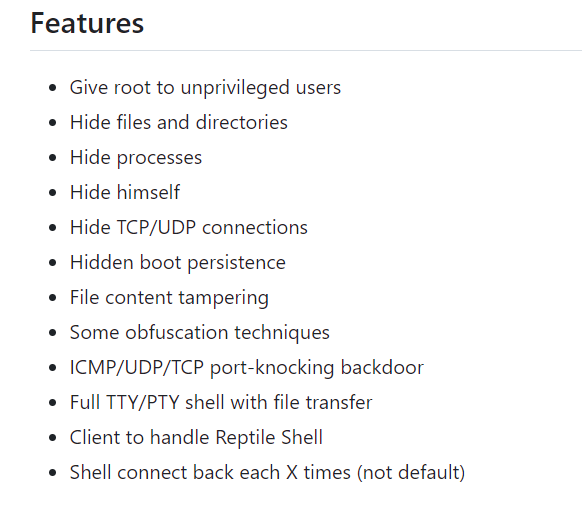
The stream ends with the attacker getting error messages, so its unclear if they were successful in setting up the rootkit, but at least we can answer the last couple of questions in this task:
The attacker downloaded something from GitHub. What is the name of the GitHub project?
reptile
The project can be used to install a stealthy backdoor on the system. It can be very hard to detect. What is this type of backdoor called?
rootkit
We’ll finish task two and this challenge on the next post.

