
I decided to make my first writeup on the Pickle Rick box from TryHackMe.com. I enjoy the show, and its supposed to be an easy box, so lets give it a go.
After getting the machine spun up, I start with a nmap scan. I have seen a variety of go to, initial nmap commands, but I like to start with:
nmap -A -T4 <TARGET IP>This will scan the most common 1000 ports, along with OS detection, version detection, script scanning and a traceroute. Its usually a pretty quick scan and is enough to give you an idea of where to start. I will usually run another scan right after this, removing the T4 and A flags while adding the -p- flag, to scan all 65535 ports, just in case there are uncommon ports that are open.
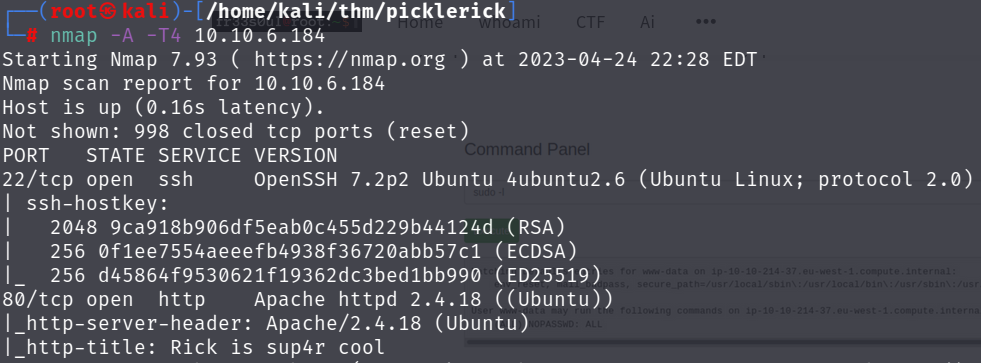
So we get back port 22 running SSH and port 80 running http. In the real world it would be best to check the versions of both services running, in this case OpenSSH 7.2p2 and Apache httpd 2.4.18, for any known vulnerabilities. Having a little experience with boxes I’m pretty sure that won’t be necessary here, so I am going to start by taking a look at the web server running on port 80.
The homepage loads with a message from Rick asking for us to help him locate the ingredients he needs for his pickle reversing potion. He tells us we need to logon to his computer to get those ingredients, but he doesn’t remember his password. I always like taking a quick peek at the source code of the site just to see if there are any comments left in the html code. I don’t know how often that actually happens in the real world, but in CTF style boxes its not too uncommon.
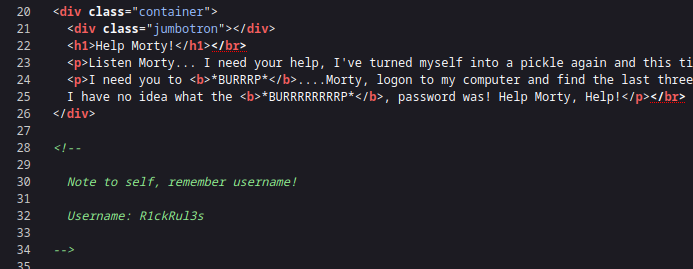
And what do you know, we find the username R1ckRul3s. We can save that to our notes and keep moving along. The next thing I like to do on web challenges is a directory search to see what other pages might exist for the site. Similar to my nmap methodology, I use a tool for a quick search to pick up some of the more common directories, just so I have a place to start, and then run a more in-depth search using another tool. That way as I am exploring what I found, I can have the other tool digging for more uncommon directories.
I like using dirsearch for the quick scan. I’ll ask it to search for php and html extensions, and exclude any responses that come back with 400, 401, or 403.
# dirsearch -u <TARGET IP:PORT> -e php,html -x 400,401,403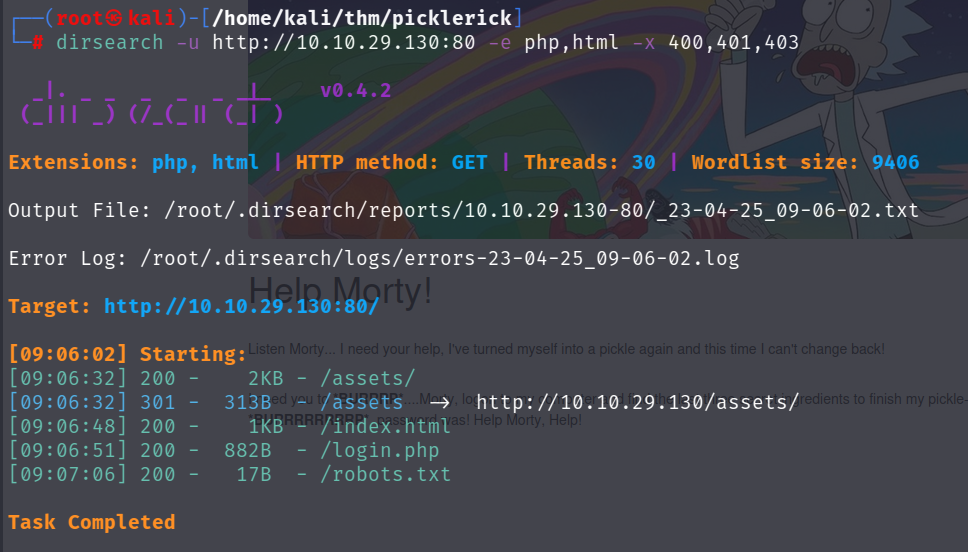
Nice! This gives us a few places to start looking. I’ll start a ffuf scan at this point using a much bigger dictionary list to pick up any potential obscure directories or extensions that might have been missed. Since this is an easy box, chances are it won’t find anything else, but you never know.
I’ll start off looking at the robots.txt file. I will usually try to read this file whether it shows up on a scan or not. It looks like Rick is trolling us, as the file doesn’t appear to contain any valuable information, just a ‘Wubbalubbadubdub’. Anyone familiar with the show would know that is one of Rick’s catch phrases. So next lets take a look at the assets folder. This also appears to be a dead end, as it only contains some pics and default css/js code.
Next on the list is the login.php page. This brings us to a standard looking login page asking for a username and password. I will usually hit a login page with the standard admin:admin attempt, or even admin:password123, as that will sometimes work with CTF style boxes. But remember from earlier we were able to get a username of R1ckRul3s. I had fired up Burp Suite to try and brute force the login with that username and some common passwords when it dawned on me that the information from the robots.txt file might not be useless after all. So I used Wubbalubbadubdub as the password and bingo, we’re in!
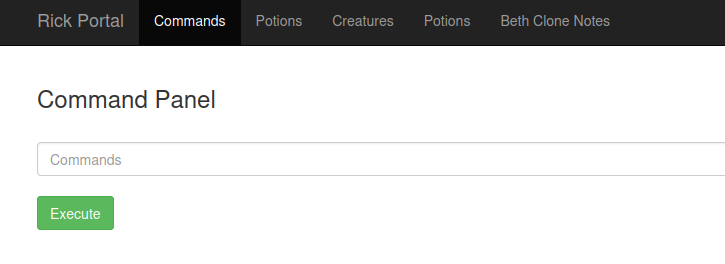
Exploring the admin portal doesn’t provide a whole lot of options, as every link in the menu bar points to denied.php, telling us only the REAL Rick can view that page. So let’s play around with the command panel and see what commands it allows us to execute. The ‘whoami’ command lets us know we are currently using the www-data user, and ‘pwd’ tells us we are in the /var/www/html folder. Running ‘ls’ displays the content of this directory. A couple of files stand out, ‘Sup3rS3cretPickl3Ingred.txt’ and ‘clue.txt’. Unfortunately the cat command has been disabled, so let’s see if there are any other commands that allow us to view files.
There are many commands that can facilitate reading a file, and I decided to try the ‘strings’ command first. Thankfully that command is not blocked, and running ‘strings’ on Sup3rS3cretPickl3Ingred.txt gives us the first ingredient.

Reading the clue.txt file just tells us to look around the file system for the other ingredients. We got two more to find, so lets get to it.
I like to know what users are on the system and a quick way to see that is through the /etc/passwd file. So running the ‘strings’ command on that file gives us a long list of system users, and the only one that stands out is the ubuntu user with a uid of 1000. I also like to look in the /home folder, and that reveals another user of ‘rick’ that did not appear in the /etc/passwd file. I went back and looked at the page source to see if maybe the display had been cut off and did not show the entire file, but that did not reveal any more of the cat file. It did however reveal a base64 code in a comment near the bottom of the page. Hoping this might lead to another clue, I started decoding the string using an online tool. After about 6 or 7 rounds of decoding, it finally reveals the next clue….’rabbit hole’, lol.
Next I decide to go ahead and ‘ls’ the rick folder and it lists the next ingredient under a file ‘second ingredients’.

Two down, one to go.
I spent a little time digging around some of the other folders and didnt find anything, so I figure the last flag is more than likely going to be in the /root directory. The only way to access files in that directory is with root/admin privileges. I really want to get a shell at this point, although after reading some writeups after I was done I realized this was a bit overkill.
I first check to see if I can run a command to upload a file using ‘wget -h’. It looks hopeful as the help file is displayed for the wget command. I also know the server is running php, so I run a ‘php -h’ command and it displays the help file for the php command. So I know I can potentially upload a file, and run a php file, so I use the php reverse shell code from pentestmonkey to craft my payload and upload it to the /tmp folder on the server. I use netcat to open a listener on my attack machine, then run ‘php /tmp/shell.php’ on the target server and boom, I get a shell. Its a limited shell, so I use python to create a tty shell to provide a little more functionality.
Now that I have a shell I plan on starting down the linux priv esc path. Just as I was about to upload linpeas.sh and start digging through all the potential vulnerabilities, I decide to run a ‘sudo -l’ command to see if I have any sudo privileges. Much to my surprise I have access to ALL with NOPASSWD.

I guess no linpeas is needed at this point lol. I run ‘sudo su’ to switch into root, and now we own the machine. I navigate to the /root directory and find the last flag.

Box solved!

